Azure API Gateway
This document outlines steps to enabled Exto through an API Management framework. For more information on using centralised API Management, its benefits, architecture, and uses
Step 1: Generate PAT Token
Step 2: Store the Token in Azure Key Vault
Step 3: Create or Edit Existing Endpoint
Step 4: Add Inbound Policy
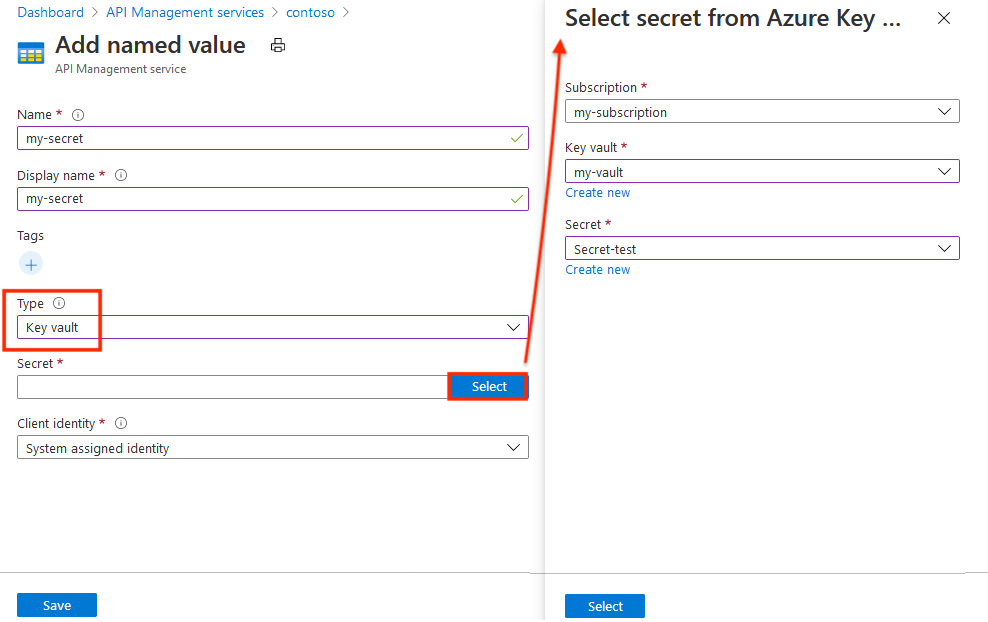
Step 5: Add Named Value to Read Value from Key Vault
Step 6: Set Header Inside the <send-request> Tag
<send-request> TagReference
Last updated